Bolt.new: The Public Workspace Roulette - Stackblitz's Unintended Feature

In the world of technology, there's often a fine line between a "feature" and a "vulnerability." Recently, I stumbled upon a very interesting quirk in Stackblitz's new service, Bolt.new, and well... let's just say it might make you question your understanding of the word "secret."
🚨 The Vulnerability That Isn't a Vulnerability
Allow me to take you through what Stackblitz insists is "intended functionality" and not a security vulnerability. The Bolt.new application includes a feature to import arbitrary Stackblitz workspaces by making a simple HTTP POST request. The interesting thing here is the slug. It turns out that this workspace identifier (which always starts with "sb1-") is just followed by six alphanumeric characters, all lowercase. That means it can be iterated over, making it susceptible to brute force attacks. No rate limiting, no protection—just pure public roulette with potentially sensitive information.
This vulnerability allows anyone with enough patience (or a simple script) to iterate through all possible slugs and access arbitrary workspaces. These workspaces could contain anything from API keys to confidential credentials to proprietary code. And the best part? This works because, as Stackblitz says, it's all public by default.
So, with a bit of creative automation, an attacker could theoretically iterate through the slug and access workspaces that were supposedly "secret." How's that for intended functionality?
📲 The "It's Not a Bug, It's a Feature" Reaction
You might think this would be a big deal, but Stackblitz has a different take. Their response on GitHub was essentially: "Hey, this is how it's been since 2017! These projects are public by default, just like they've always been." But here's where it gets a little humorous—or scary, depending on your perspective.
Stackblitz projects have always been public, but with Bolt.new, people are now dropping in environment variables and sensitive data. So, instead of calling this a vulnerability, Stackblitz frames it as user confusion about default visibility. It's not a security breach; it's just that users don't know how public public really is. Oh, and if you're a non-premium user? Yeah, no private workspace for you.
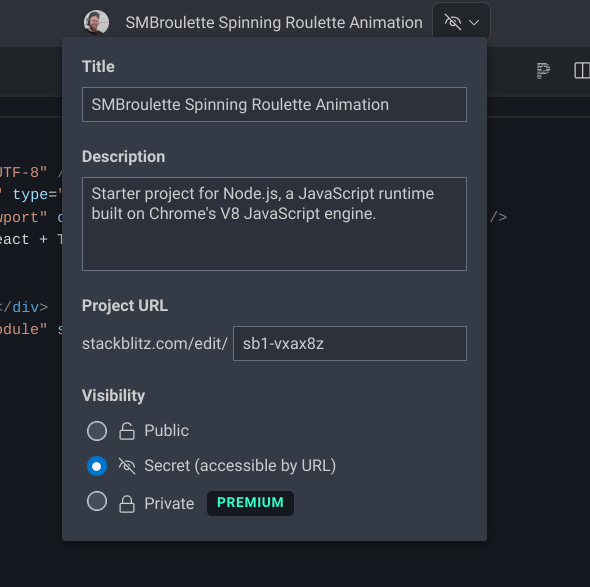
To illustrate, here's a delightful screenshot from Stackblitz, where you can set your workspace visibility to "Public," "Secret (accessible by URL)," or "Private (Premium)." Spoiler alert: "Secret" here just means anyone with the URL can access it. It’s like leaving your house door open and saying it’s "secure" because only those who enter your address can get in. The kicker? Non-premium users don’t even get the option for real privacy.
🛠️ The "Fix"
Now, thanks to what they describe as a lot of users putting environment variables in their workspaces, Stackblitz has decided to change the default visibility to private. They're on track to make this update by the end of the day. I can almost hear them saying, "You wanted private workspaces, right? We'll give you private workspaces, but we're still calling it a feature."
They even posted on Twitter to say, "This is not a security vulnerability, it's just an issue with folks having projects be public instead of private." Well, you heard them, folks. If you accidentally left your secret code or API keys in a public Bolt.new workspace, that's not a vulnerability—it's just you misunderstanding how "public" your data is.
🤔 Final Thoughts
We can debate whether this is a vulnerability or merely unintended behavior until the cows come home. But at the end of the day, the reality remains: if you're a non-premium user, your workspace is not truly secure. In the absence of proper protections like rate limiting, better slug complexity, or even just reliable privacy settings for free users, the door is still wide open for exploitation.
So, if you want my advice: treat your Bolt.new workspaces like they're public, unless you know for sure they’re behind a lock (and are willing to pay for that lock). Otherwise, you might just find your "secret" project making the rounds on the internet roulette.
💡 Stackblitz, You Might Want to Reconsider
To Stackblitz: maybe it's time to take a more serious look at how your users understand privacy. I get it, defaults can be tricky. But downplaying the importance of privacy settings, especially in a dev world where sensitive data leaks are rampant, doesn’t do anyone any favors. Let’s try not to brush off real concerns as just user misunderstandings.
To everyone else: stay vigilant, understand how "public" your workspaces actually are, and maybe invest in some premium privacy if you don’t want your secrets out there for the taking.
References:
Let's see if someone looks at my mal ... pic.twitter.com/wEgzYYBooG
— Ⓒhrstphⓡ ㋡ ☠☢💣 匚尺卂山ㄥ丨几Ꮆ 🎯 ʘ.0.ʘ.Ѳ/0 💥 (@schniggie) October 15, 2024


