Operation Triangulation
The guys from Kaspersky revealed a crazy iOS attack chain that they caught in action against some of their employees.
The complete attack chain is just millions of $$$ in exploit prices.
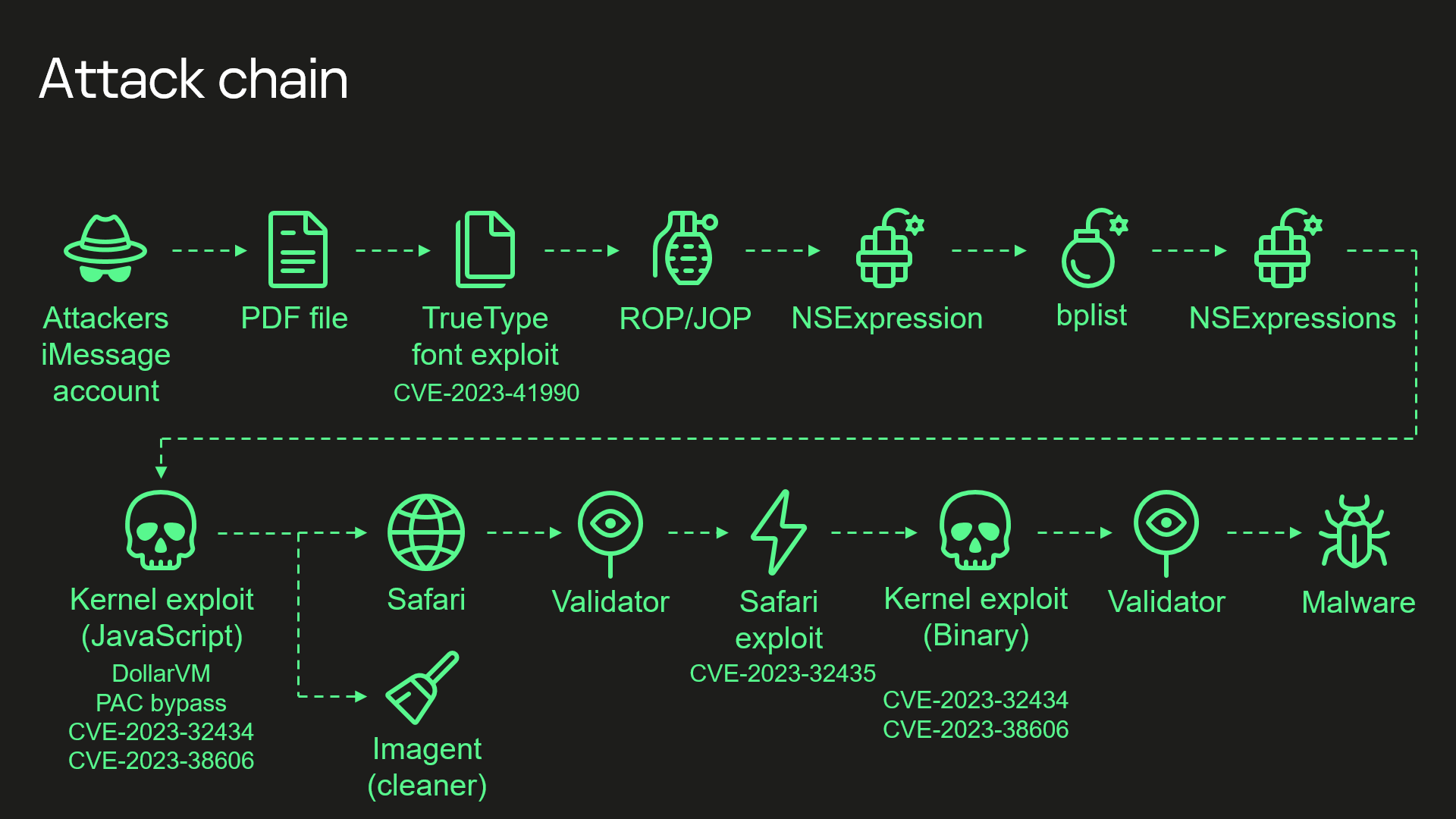
For example, the initial PDF exploit is caused by a True Type code part from the early 90s. 25 years ... I love well-hung vulns :D
The guys did a really great job in capturing and understanding all stages of the attack chain.
One fun fact, they found a list of 40 MD5 hashes. By hardcore bruteforcing (Thanks to MD5 :D) they were able to reveal most of that hashes. It turns out, that's Apple IDs used by the attackers to send out the first attack step.
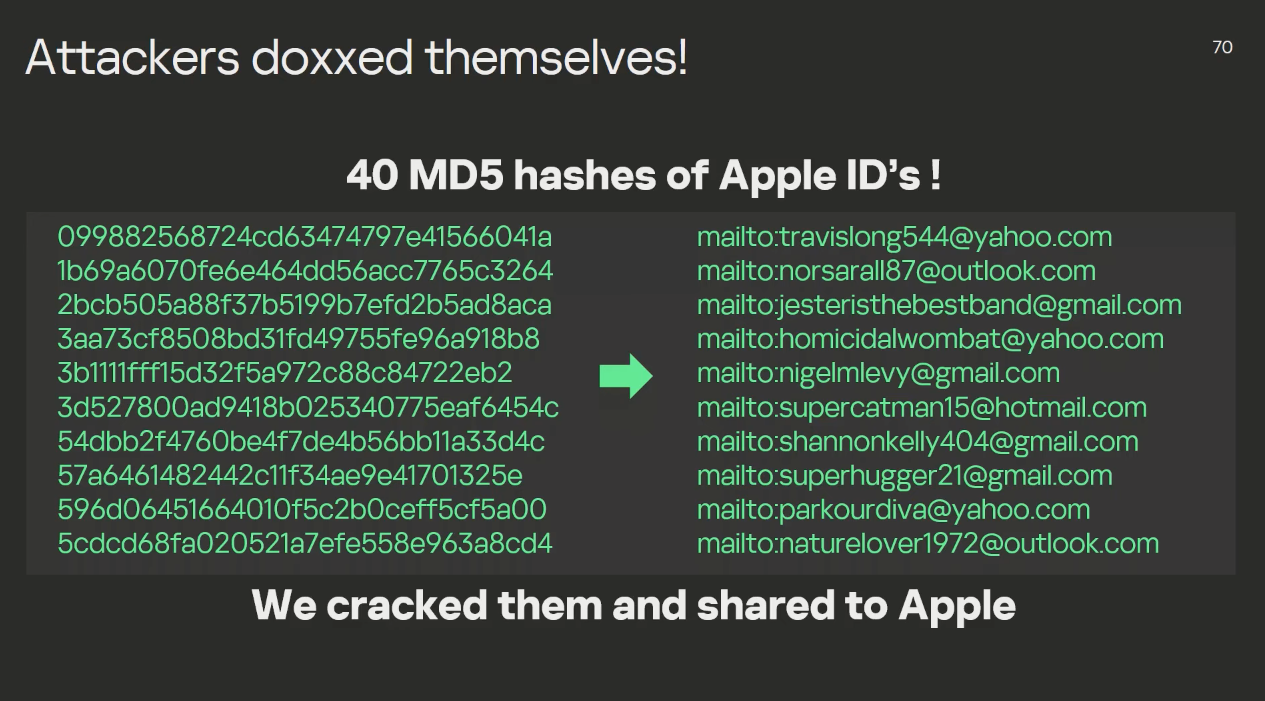
OPSEC is hard as always, also for attackers.

The full story can be read here https://securelist.com/operation-triangulation-the-last-hardware-mystery/111669/.
There is also a great talk from this weeks 37C3: https://media.ccc.de/v/37c3-11859-operation_triangulation_what_you_get_when_attack_iphones_of_researchers.

